Mac Spoofing
In Business, Official Blog, TechnicalWHAT IS MAC SPOOFING?
Mac spoofing is a term which consists of two different terms MAC ADDRESS and SPOOFING.
WHAT IS MAC ADDRESS?
Full form of mac address is media access control address. This address helps a router to identify your device, or we can say that this an identification number of your wireless device. You can find your routers mac address on this plate provided below your router.
WHAT IS SPOOFING?
Spoofing comes from the word spoof which means To simulate a communications protocol by a program that is interjected into a normal sequence of processes for the purpose of adding some useful function.
After get to know about both terms we will come to our main topic of today which is mac spoofing.
basically, mac spoofing means to change your device mac address. In old devices, you dont get the option to spoof your mac address but you can do if you have root access to your device. In todays world if have bought a router then definitely get an option to change your mac address.
WHY TO SPOOF YOUR MAC ADDRESS?
We have learned about mac spoofing, But why we do mac spoofing why we change our mac address. So there are many advantages of mac spoofing.
ADVANTAGES
Free internet: ? there are many places where can get free wifi without entering any password but they have enabled mac filter. you can net connect to there wifi without changing your mac address.
To be anonymous: ? If you want to connect a wifi but you dont want to be get traced, anyone.
Identity Protection: As I told you its your identity on the network so you can protect your identity on that network.
bypass mac filtering: ? in many places, a specific mac address is allowed to connect so you change your mac address then you are able to connect to the wifi network. Or in some cases someone has blocked you mac address then you change and connect with that wifi network.




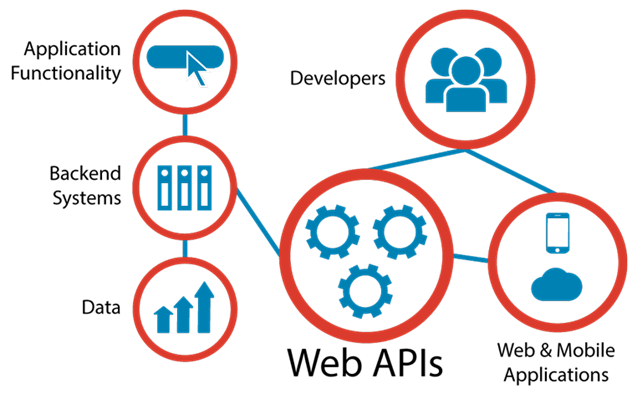
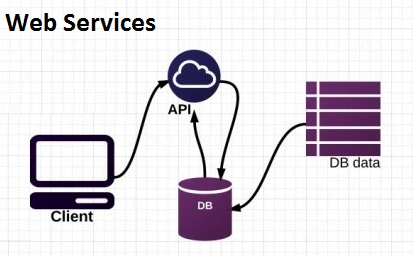
 Are you new to the world of web development then you must have to listen to the word “API” and might be curious about it too? So in this article will get know what is API and some terms related to it with our daily life examples. So let’s get started.
Are you new to the world of web development then you must have to listen to the word “API” and might be curious about it too? So in this article will get know what is API and some terms related to it with our daily life examples. So let’s get started.