How to Get Toll Free Numbers?
In Business, Official Blog, Tech-BLOG, TechnicalToll-free numbers are telephone numbers with distinct three-digit codes that can be dialed from landlines with no charge to the person placing the call. Such numbers allow callers to reach businesses and/or individuals out of the area without being charged a long-distance fee for the call.
Toll-free numbers are particularly common for customer-service calling. Toll-free service has traditionally provided potential customers and others with a free and convenient way to contact businesses. Customers can also send text messages to toll-free numbers, so long as those numbers are “text enabled,” and businesses can send texts in response.
How are toll-free numbers assigned?
Toll-free numbers are assigned on a first-come, first-served basis by entities called “Responsible Organizations” or “RespOrgs.” Many of these entities also provide toll-free service. RespOrgs have access to a toll-free database that contains information regarding the status of all toll-free numbers.
Hence, you can also contact Jain Software for assigning a toll-free number. Jain Software is Central India’s Fastest Growing Software Company providing a broad range of software services, solutions in strategy, consulting, digital, technology and operations.
So, it also provides toll-free numbers to different businesses/organizations, etc. If you are interested in assigning the toll-free number for your business or organizations, you can contact to Jain Software by calling on +91-771-4700-300 or you can email us on Global@Jain.software.





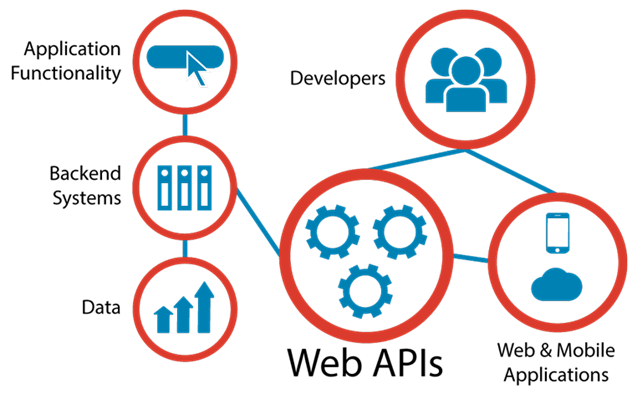
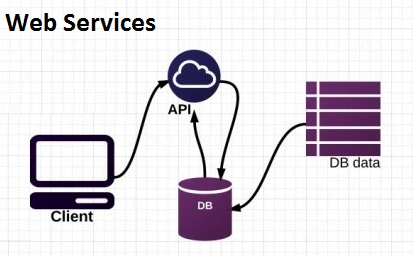
 Are you new to the world of web development then you must have to listen to the word “API” and might be curious about it too? So in this article will get know what is API and some terms related to it with our daily life examples. So let’s get started.
Are you new to the world of web development then you must have to listen to the word “API” and might be curious about it too? So in this article will get know what is API and some terms related to it with our daily life examples. So let’s get started.