Discover the Power of Technology with Jain Software
In Official Blog, BusinessTechnology is the engine for change, development, and productivity in the current world especially for the growing industries. Be it the field of health care, or business comprising of electronic commerce every sector is experiencing a revolution with technology being a panacea to all sectors. Jain Software, one of the prominent names in the sphere of IT, takes part in delivering some of the most innovative solutions that help companies make the most use of technologies. In this blog, let’s understand how Jain Software is future-readying several industries and why entrusting Jain Software is a decision that can turn the trajectory of your business to the right direction.
The Position of Technology in the Current World of Business 
The use of technology systems has become common in the current day business environments where firms are now more strategic and more relevant for the purpose of advancing their capabilities. There are many known benefits that new technologies in an organization may offer such as improved efficiency, decreased expenditure, and better decision making. In the current world, organizations that want to regain a competitive edge must collaborate with a technology firm such as Jain Software.
Jain Software: Just as IDEO has inspired innovation in design, Silver has been inspiring innovation in itself for almost a quarter of a century.
Jain Software was established with the mission of offering quality Information Technology solutions that could meet the clients needs. The services provided by the company include custom software development, ERP solutions, Web and mobile application development, Digital marketing and web hosting etc. , through its subsidiary MNC Host. From healthcare to e-commerce, education to hospitality, Jain Software has knowledge within such a wide range of sectors they are the perfect choice for small to larger business.
Transforming Healthcare with Technology
Today’s healthcare sector has not remained the same due to the introduction of technology in the practice. Jain Software has been a pioneer of this shift, providing applications for providing better patient care, operational efficiency and better data capture.
1. ERP Solutions for Healthcare:
Jain Software focuses its ERP solutions on some challenges that are facing the healthcare industry. These solutions combine different functions like patient handling, charges, stock, and human resource in one system which helps the healthcare organizations for their efficient running. Jain Software’s ERP systems resolve mundane tasks and grant ready access to data as a result the providers of healthcare enhance the quality of their services and the outcomes of their patients.
2. Customized Software Development:
Every health care center has its individual requirements, and at Jain Software, we do realize it. Focused on creating exclusive software solutions for hospital, clinics, and other health care organizations, the company has its core expertise. When it comes to a patient management system or telemedicine platform, or even a diagnostic software, Jain Software realises how custom software solutions can improve operational excellence while increasing patient satisfaction.
Enabling of E-commerce with Intelligent Solutions
The ‘‘e-commerce industry is growing inexhaustibly, and enterprises are ever in the lookout for strategies of enhancing their online visibility and/or consumers’ satisfaction. Recently established Jain Software provides its clients with a wide range of e-commerce services aimed at promoting their success in the world wide web environment.
1. E-commerce Platform Development:
Jain Software developed its e-commerce programs as shopping assistants for customers, as well as managing platforms for businesses. Some of the facilities like inventory, payment gateway services and customer relationship management make Jain Software’s e-commerce solutions useful for businesses for reaching and selling more to their customers online.
2. Digital Marketing Services:
In today’s challenging environment, having a proper channel of advertising your products or services is crucial for the success of the business. Jain Software’s services in this area are SEO, SMM, PPC Advertising, and Content Marketing. By adopting these strategies, the firms are able to enhance their presence online, many clients are reached, and sales improved. Obviously, at Jain Software, emphasis is given to the accurate targeting of marketing with an aim of achieving the largest return on investment.
Unification of business processes and integration of Enterprise Resource Planning Solutions
Implementing ERP systems are important for any organization with a desire to integrate its business functions and processes to enhance on efficiency. Jain Software’s ERP solutions encompass all areas of business, these being the financials, logistics, and employees.
1. HRM Solutions:
Human resource is one of the most important organizations in any firm but handling it is a tiresome and a time-consuming activity. This is why Jain Software’s HRM solutions help in making the process easy by including features that help in automating functions like payroll, on-boarding of workers, performance appraisal and compliance. This also helps cut costs on administrative work while displaying a positive outlook towards employees because HR operations are made smooth and clear.
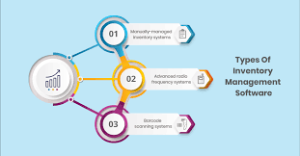
2. Inventory Management:
Stock control is an important factor essential to decreasing costs and from the other side to provide products for various needs. Using software solutions from Jain Software, the inventory holding gives real time information of stock, automated the reordering and tracking of inventory between different locations. This assists in the reduction of stock out and over stock conditions which lead to a better operation of the business.
Optimizing on the Customer Experience with Customized Mobile Applications
As the world is shifting progressively mobile having a custom mobile app can provide the business with an almost direct access to its customer base. Yet, Jain Software focusing on building apps for business and available apps are a retail app, loyalty program or customer service portal.
1. User-Friendly Design:
Thus, let me emphasize the significance of the mobile application’s User Interface and User Experience (UI/UX). The designers and developers of Jain Software’s are skilled and are able to develop attractive and user-friendly applications. This aspect of design enables Jain Software to guarantee its customers have the best time using the app hence using the app more often.
2. Integration with Existing Systems:
When one is developing an app for businesses that already have some systems in place like ERP or CRM it is important that the business mobile can easily relate with those systems. In their custom mobile apps, Jain Software takes care to integrate with the existing setup so that data can be easily transferred from the mobile app to the other structure. It improves the general functionality of business processes and can create a coherent client satisfaction perspective.
Make Sure Your Digital Property Is Safe from Bad Hosting
Thus, high-quality hosting services are a leeward for companies operating in the digital age, so that their web resources are always open to consumers. Through its wholly owned subsidiary MNC Host, Jain Software provides website hosting services for business purpose as outlined below.
1. Scalable Hosting Solutions:
Small business, or large enterprise – Jain Software’s hosting solutions can be customized to our clients’ preferences. Based on shared hosting to dedicated servers MNC Host offers a stable and secure connection that will guarantee uninterrupted work of your sites and applications. Technicians are always ready to assist clients and clients’ businesses are well secured at any given time day or night.
2. Domain and Server Management:
Whether or not you have a specialized technical staff today, holding your own domain and server can present many challenges to your company. Jain Software specializes in domain registration services, host management, and other related services to allow an easy management of the online business. This is particularly so since Jain Software manages the technical aspects of an operation this leaves your hand free to do what it does best – the running of a business.
Conclusion
And in a world where commercial breakthrough is heavily driven by technology, it has never been more critical to build a solid relationship with a technological ally. Jain Software’s all round, end to end service offerings of custom software development, digital marketing and web hosting make it an industry giant. Jain Software helps businesses unleash the power of technology and provide value to them for making their business processes more efficient. No matter what line of business you are in: healthcare, e-commerce or any other, Jain Software can assist you in navigating the new business environment. Learn more about technology with Jain Software and revolutionized your business.


 Major assets of Jain Software include a flexibility which allows the company to provide a broad spectrum of IT services in response to the needs of every customer. When it comes to software needs, whether it is an ERP system, an e-commerce platform, or application development, Jain Software has all the right skills for providing exactly what your business requires.
Major assets of Jain Software include a flexibility which allows the company to provide a broad spectrum of IT services in response to the needs of every customer. When it comes to software needs, whether it is an ERP system, an e-commerce platform, or application development, Jain Software has all the right skills for providing exactly what your business requires. Now in the twenty first century, the popularization of online shopping platform has now become the norm. Whether you are a new born company entering the world of e-commerce or an existing business planning to take your business online, it is imperative that you have a strong e-commerce platform in today’s competitive business environment. With the latest SoS and their vast consultancy services, Jain Software is set to assist organizations to maneuver through the jungle of e commerce and create astounding prosperity.
Now in the twenty first century, the popularization of online shopping platform has now become the norm. Whether you are a new born company entering the world of e-commerce or an existing business planning to take your business online, it is imperative that you have a strong e-commerce platform in today’s competitive business environment. With the latest SoS and their vast consultancy services, Jain Software is set to assist organizations to maneuver through the jungle of e commerce and create astounding prosperity.