In Official Blog, Technical
Â
Â
Application Requirement Specification
Â
Â
Â
Â
Prepared by
Sohil Jain
AppleOfficer Inc
Jain Software Foundation
- Introduction
This document is prepared in order to determine an Application requirement specification for The Social App. The Social App is a social network on which people can add their friends, share videos and photos, send and receive messages, comment on the links etc. In order to gain an overview of the report, firstly, the purpose and scope of this document will be given, the overall description of the Network App is followed. In addition to these, system features such as uploading a photo, sharing video, adding friend etc. are described deeply. After mentioning about the introduction of the system, the specific requirements will be addressed for it. In the final part, functional and non-functional requirements will be addressed.
- Purpose
The SRS is needed to evolve as the development of the Application product processes. The purpose of this document is to give a complete description of how The Social App system can be developed. This document is to provide information about what the software product is to do to users and establish an agreement between them. In addition to these, it provides a basis for validation and verification. The issues which are basically addressed are functions such as adding friends, uploading photos, adding videos, chatting, ratings, timeline and tagging, external interfaces, creating groups and the design constraints of the system.
- Scope
The name of the product is The Social App. It is a social network that connects people. The aim of App is to provide information to the users about the events and the people whom they know. The users can add friends, share videos which they want their friends to watch; upload photos, comment on their friends’ sharing, chatting with their friends. Moreover, people can create social groups or communities for such as university clubs, football clubs or for social awareness. People can be informed about the events with the help of these groups or their friends.
- DEFINITIONS, ACRONYMS, and ABBREVIATIONS
When the user logins The Social App, they can see their home page, which is named as “Explore†that provide users to see what their friends share, what their friends write their status and other public videos uploaded by the users.
- Overall Description
In this section, background information about what type of requirements the system should have will be provided briefly.
- Product Perspective
The The Social App is an independent and world-wide social network Application. Every person can use it online without a fee. People from different regions of the world can connect to it and exchange information with other people. In order to control the contents of the sharing and comments done by the other people, the app has also a control mechanism. People can deliver their complaints about any part of the application to the “Administratorsâ€. Then, “Administrators†might take appropriate actions according to the complained situation which is against the rules.
- Product Function
After creating an account and starting to use the App, the first thing he or she sees is the “Explore” that has posts from the users and suggestions of the pages they can like. The user will go to his profile and add the required details such as the profile and timeline picture. The user will search people by their names and can send an invitation to them to add as a friend or directly send a message. If the person accepts the invitation, these two persons become friends and can interact more closely such as sending messages to each other, like each other’s posts, can comment on posts. Any user can share his/her status like whatever he is thinking, wherever he is or his current mode. Friends of this person can make a comment on that. Furthermore, if a user shares a photo, video, link or anything, any friend of that user can share that shared item also. Users can upload photo and video to their profiles.
- User Characteristics
The Social App does not require any specific computer knowledge to use it except developers and administrators of it. Standard users are thought to be from any age, any gender and from any nationality who can use just computer’s browser. On the other hand, administrators and potential developers need a high level of expertise to understand web technologies.
- Constraints
Being a social network website, the software should ensure the safety of information given by the user and provide some privacy settings options to the user. Firstly, the app provides people the right to choose the category of people who will be able to view their shared items, to allow comments on their shared items, allow comments on gallery items, whether they want to share their information with others, to allow show their friends list or the gallery. Some users may not desire the access of some people to their shared items and information. Users can set their privacy settings to prevent some people’s access to their information or any field if they want to. Secondly, It cannot sell the private information of users to someone else. However, if the user permits, an application can access to some information of the user.
- Specific Requirements
In this section, all software requirements will be explained in detail. All requirements are divided into two groups as functional and non-functional.
- External Interface Requirements
In this section, external interface requirements for user and communication channels will be described in order to clarify the relationship of this software with other entities and systems.
In the first part, user’s interfaces will be explained with the layout information, textual items and error handling types for two types of users of the system, as standard users and administrators. In the second part, communication interfaces of our system will be described in order to explain the relationship with other systems which are sharing information with the app.
- User Interfaces
Standard users shall be downloading it from the play store. It has a login page and users must log in with their e-mail addresses and passwords. After a successful login, they shall be taken to their “Explore†which is their homepage thereafter. Since they are logged into the system, there must be a log out button and their profile names at the top of the page until they log out of the system.
Being a social network, a direct link to the list of “Friends†shall be listed in the “Hamburger†menu, located at the left top, “Settings” include “Logout†and “Accountant Privacy Settingsâ€. At the top, there shall be “Exploreâ€. “Search†field which lets users search for their friends and posts. All other features of the system shall be reachable by the menu as a left sidebar such as Explore, News, Profile, Notifications, Messages, Friends, Nearby, Favorites, Search and settings. “Creating Event†which is related to “Events†feature, shall be reachable from the related features menu.
Since standard users can use different types of features, there shall be different interfaces for each of them and they will be described separately:
- Sign Up
Sign up to use the app and to make sure the user is an authenticated user. Fill out all the details properly to be a verified user and able to use the app.
- Confirm button makes sure you think twice before agreeing to the terms and conditions of the
- Referral user Id is replaced with phone number field that is optional for the user.
- User id is a unique and is mandatory for every user to enter during sign up.
- Sign In
Enter user id/email id and password to access the app from anywhere and anytime. The credentials are same, entered during the sign up. You can’t login without your user id and password.
- Home page (Feed)
Home is the first thing you see after logging into your account where you see the posts posted by the users, likes, comments etc. Home and Video pages are in tabbed view. Swipe right to left to switch to video tab. Home page has your profile picture and timeline picture as well. Both will be visible in every page whether it is your home, profile or any other page. It is also same when any one messages to their friends.
A user is suggested or displayed by its user id instead of his real name or any other information.
- Post
A user can post anything. A post can be an audio, video, image or simple text.
- Like button is different from the regular like buttons.
- Share button is different from the regular share buttons.
- Five star ratings are only for the videos.
- Counter timer is added with every post that counts down from 24 hour to zero.
- Post owner can see the list of activities (likes + comments + share) on his post.
- Three vertical dots on the top right corner of the post provide options share and delete.
- Video
- A video is played on a single click.
- After watching a video users can rate it out of five stars. Rating is only for the video and not for the other media.
- Owner of the post can see the list of users who have liked or viewed their post.
- When clicked on comments only comments posted by users are posted without the media.
- Video has a view button that shows that list of people who have viewed the post.
- Video page is the streaming page. Streaming page only displays pages that are public to the users.
- Friends Page
Friend’s page has 4 tabs
- Friends
- Followers
- Following
- Groups (communities)
- Pages
- Chat page: It hast two tabs one displaying the chats with friends and other tab displaying the list of chats with business people.
- Search page: Users’ suggestion below search is not displayed.
Search results are displayed in two categories
- Settings page: Remove the allow comments from settings page.
Remove gifts and private messages from push notifications.
Remove referrals.
General settings lets you edit name, DOB, contact number and user id.
- Postings page: User can select multiple images to post but only single video at a time.
- A video with maximum length of 1.10 seconds and minimum of 30 seconds is allowed.
- Preview of the selected item is also available in a good quality.
- Add camera recording option.
- Add an option to make comments as public, private or no comments at all.
- Talent tag field: Create a talent tag to add talents into user’s talent list
Talent tag fields
Photo:
- Painting
- Embroidery work
- Photography
- Story writer
- Poetry
- Art
- Handloom
- Designer
- Paper Art
- Cryptography
- Tattoo
Video
- Dancing
- Singing
- Movie
- Acting
Status has maximum limit of 250 words. And the preview of the selected media is large.
- Profile page: The timeline pic is vertical rectangular pic. The profile pic is a 6 cone star pic and is overlapping with rectangular pic in the background. The same page has Social ratings and talent ratings.
- Navigation
All pages are shown in floating action button. On every page it is displayed and different icons represent different pages. The FAB always remains on the screen and background becomes blurry when clicked on it. The icons open in vertical and horizontal both the directions and it closes when clicked anywhere else on the screen.
FAB Style Sample
Page refreshes when clicked and hold for 3 seconds.
Change background button colors.
- Banner
Ad banner is on the top of the every page with dimensions 320×75.
- Functional Requirements:
- The system shall check whether the administrator chooses at least one action.
- The system shall not let administrators take actions to the complaints that are completed.
- Nonfunctional Requirements
Performance Requirements:
The system shall be available from all over the world at all times. Being a social network, any interruption in the sharing chain will cause people to give up on App, therefore it is essential that the system shall be available at all times. The system shall not be affected by the number of active users in the system until half of the registered users become active. Being a worldwide network, assuming that half of the registered users are reaching to the App is a legitimate and necessary requirement.
Design of the system shall arrange the content size as compatible with different platforms, such as mobile phones, tablets, and desktop computers. Since App is based on sharing with friends, the design of the system shall let the high level of mobile access. Design of the system shall let different languages to be shown without affecting the general layout and operations. Being a worldwide network, different language sets shall be able to show as the main language of the website without creating any obstacles on the operations.
Â








 In this digital world, we are obsessed with the technology. Technology is changing every second. With the emergence of technology, the threats in the cybersecurity are increasing every day.
In this digital world, we are obsessed with the technology. Technology is changing every second. With the emergence of technology, the threats in the cybersecurity are increasing every day.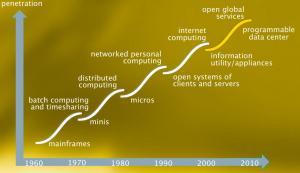 Threats to organization
Threats to organization Banking, Financial Services and Insurance (BFSI): The BFSI sector is under growing pressure to update its legacy systems to compete with new digital-savvy competitors. The value of the customer data they hold has grown as consumers demand a more convenient and personalized service, but trust is essential. Some 50% of customers would consider switching banks if theirs suffered a cyber-attack, while 47% would “lose complete trust†in them, according to a recent study. A number of major banks around the world have already been subject to high-profile cyber-attacks suggesting that the sector needs to improve its approach to risk. Financial firms should invest in security applications that are able to adapt to the future of banking to ensure comprehensive, around-the-clock security. Shared Ledgers will feature prominently in the future of the BFSI sector, the best-known example of which is Blockchain, which forms the backbone of cryptocurrency Bitcoin. The blockchain is a database that provides a permanent record of transactions. It leaves an undisputed audit trail that can’t be tampered with, meaning it could completely transform security in the BFSI sector.
Banking, Financial Services and Insurance (BFSI): The BFSI sector is under growing pressure to update its legacy systems to compete with new digital-savvy competitors. The value of the customer data they hold has grown as consumers demand a more convenient and personalized service, but trust is essential. Some 50% of customers would consider switching banks if theirs suffered a cyber-attack, while 47% would “lose complete trust†in them, according to a recent study. A number of major banks around the world have already been subject to high-profile cyber-attacks suggesting that the sector needs to improve its approach to risk. Financial firms should invest in security applications that are able to adapt to the future of banking to ensure comprehensive, around-the-clock security. Shared Ledgers will feature prominently in the future of the BFSI sector, the best-known example of which is Blockchain, which forms the backbone of cryptocurrency Bitcoin. The blockchain is a database that provides a permanent record of transactions. It leaves an undisputed audit trail that can’t be tampered with, meaning it could completely transform security in the BFSI sector.

 Training: The most revolutionary use of Virtual Reality has been in the training especially in those fields that involve high-risk operations like in the military, medical. Pilots and medical professionals like surgeons carry out some of the riskiest and dangerous operations in their field of work e.g. flying a military aircraft/ a brain surgery. In these situations, any untrained or undertrained person cannot be employed. Enter Virtual Reality, with modern day simulation systems a person can be trained for both situations without taking any risk on failure. Thereby providing these professionals the absolute necessary experience in handling the situation perfectly.
Training: The most revolutionary use of Virtual Reality has been in the training especially in those fields that involve high-risk operations like in the military, medical. Pilots and medical professionals like surgeons carry out some of the riskiest and dangerous operations in their field of work e.g. flying a military aircraft/ a brain surgery. In these situations, any untrained or undertrained person cannot be employed. Enter Virtual Reality, with modern day simulation systems a person can be trained for both situations without taking any risk on failure. Thereby providing these professionals the absolute necessary experience in handling the situation perfectly. Entertainment: Virtual Reality has been booming in the sector and it is believed that Virtual Reality will find the most useful in this sector from games to movies everything is being researched and developed to provide the most realistic experience to the viewer. 3D is now a thing of the past as the world is trying for 5D, a viewing experience where you can physically feel the experience like walking with the characters.
Entertainment: Virtual Reality has been booming in the sector and it is believed that Virtual Reality will find the most useful in this sector from games to movies everything is being researched and developed to provide the most realistic experience to the viewer. 3D is now a thing of the past as the world is trying for 5D, a viewing experience where you can physically feel the experience like walking with the characters.
 views, giving tours, forecasts trends and meetings. Solutions like virtual conference rooms can create a significant impact on the ways of conducting business.
views, giving tours, forecasts trends and meetings. Solutions like virtual conference rooms can create a significant impact on the ways of conducting business.